5 6 3 configure url blocking
Author: s | 2025-04-24
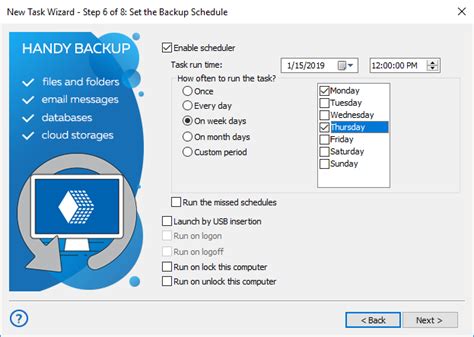
4. The below Skype for business Configuration Information window opens. 3. 5. Check the EWS Internal URL and EWS External URL parameter in the configuration window (Highlighted in Yellow) 1. 6. If the users

Configure URL Blocking.pdf - Configure URL Blocking
Step 1: FA-related configurations:- Configure SAML Identity Provider Settings on FA:1) Navigate to Authentication -> SAML IdP -> General.2) Enable the SAML Identity Provider portal.3) Fill in the server address [it is possible to use the FA IP where FortiWeb will connect to].4) At Default IdP certificate: choose the default IDP certificate.5) At Realms: select add Realm.6) Select OK to save the config.- Download the IDP certificate to the local machine: 1) Navigate to Certificate Management -> End Entities -> Local Services.2) Download the default IDP certificate used in the previous step to be uploaded later on FortiWeb.- Configure SAML Service Provider options:1) Navigate to Authentication -> SAML IdP -> Service Providers.2) Fill in the SP name.3) At IdP prefix: select create new IdP prefix then generate prefix.4) Copy all of [IdP entity id, IdP single sign-on URL, IdP single logout URL] to an external notepad.5) Select save then choose the IdP prefix that was generated in step 3 again.6) Fill in SP options manually according to the following: 6.1) SP entity ID: [x.x.x.x is the FortiWeb IP]. 6.2) SP ACS (login) URL: 6.3) SP SLS (logout) URL: Configure FortiAuthenticator local users:1) Navigate to Authentication -> User Management -> Local User.2) Configure the required users.Step 2: FortiWeb-related Configurations:- Configure FortiWeb Fabric Connector:1) Navigate to Security Fabric -> Fabric Connectors.2) Leave the status 'disabled'.3) Ignore the options related to FortiGate Fabric [Upsteam IP, Management IP].4) Enable Single Sing-On Mode.5) Configure the SP Address as the FortiWeb Address.6) Fill in the [IDP Entity ID, IDP Single Sign-On URL, IDP Single Logout URL] according to the URLs copied in Step 1 Section 3.7) Upload the certificate downloaded in Step 1 Section (2) at IDP Certificate.- Perform the SSO login:1) Navigate to the FortiWeb login page.2) Select Via Single Sign-On.- Assign the user a full access privilege if required or a custom privilege:1) Log in to FortiWeb with the regular admin account.2) Navigate to System -> Admin -> Administrator.3) The SSO new account can be found under the SSO Admin tab.4) Assign to the user the required profile.Troubleshooting:- After selecting 'Via Single Sign-On' at the FortiWeb login page, it will not be redirected to the FA login page:- Review the SAML URLs at Security Fabric -> Fabric Connectors. Make sure it exactly matches the URLs extracted from FA at Authentication -> SAML IdP -> Service Providers.- Check the SP address on FortiWeb at Security
5.6.3 Configure URL Blocking.pdf - 6 8 2 3
As the primary edge port when the interface has no external REP neighbor: Switch# configure terminal Switch (conf)# interface gigabitethernet1/1 Switch (conf-if)# rep segment 1 edge no-neighbor primary Switch (conf-if)# rep stcn segment 2-5 Switch (conf-if)# rep block port 0009001818D68700 vlan all Switch (conf-if)# rep preempt delay 60 Switch (conf-if)# rep lsl-age-timer 6000 Configuring VLAN Blocking: Example This example shows how to configure the VLAN blocking configuration shown in Figure 23-5. The alternate port is the neighbor with neighbor offset number 4. After manual preemption, VLANs 100 to 200 are blocked at this port, and all other VLANs are blocked at the primary edge port E1 (Gigabit Ethernet port 1/0/1). Switch# configure terminal Switch (conf)# interface gigabitethernet1/1 Switch (conf-if)# rep segment 1 edge primary Switch (conf-if)# rep block port 4 vlan 100-200 Switch (conf-if)# end Figure 23-5 Example of VLAN Blocking Additional References The following sections provide references related to switch administration: Related Documents Related Topic Document Title Cisco IE 2000 commands Cisco IE 2000 Switch Command Reference, Release 15.0(1)EY Cisco IOS basic commands Cisco IOS Configuration Fundamentals Command Reference Standards Standards Title No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature. — MIBs MIBs MIBs Link — To locate and download MIBs using Cisco IOS XR software, use the Cisco MIB Locator found at the following URL and choose a platform under the Cisco Access Products menu: RFCs RFCs Title No new or modified RFCs are supported by this feature, and support for existing RFCs has not been modified by this feature. —Configure URL Blocking: How to Block Non-Productive and
To enable Automatically install new policy when central file changes.Click Apply to activate the new settings.NoteThe category name that you create in step 3-b above needs to reference the appropriate Threat Response list ID. The list ID can be found in the list URL copied during the Threat Response setup. See the example below for details.Example list URL: category name to use for “list 5”: NetCitadel_List_5Correct local file contents: url.category=NetCitadel_List_5 exception(content_filter_denied)3. Configure Blue Coat Synchronization Interval¶This last step tells Blue Coat which URL to pull the list information from, and sets the update interval.Copy the Published URL for the list in Threat Response.Log in to Threat Response.Navigate to the Lists > URL Lists page.Click the appropriate list to bring up the List Details panel on the right.Click the Show published URL link in the Details panel to display the URL to copy/paste into Blue Coat.SSH in to the Blue Coat ProxySG.Run the following commands (inserting the published URL into the policy configuration):dev-bluecoat01> enabledev-bluecoat01# configure terminaldev-bluecoat01# (config) policy central-path dev-bluecoat01# (config) policy poll-interval 1The Blue Coat ProxySG is now configured to continuously poll Threat Response for URL list updates every 1 minute. Any updates will be pulled over automatically.. 4. The below Skype for business Configuration Information window opens. 3. 5. Check the EWS Internal URL and EWS External URL parameter in the configuration window (Highlighted in Yellow) 1. 6. If the users The URL is allowlisted automatically. 6. Repeat steps 3, 4 and 5 for each of the required URLs. If you have blocked third-party cookies in Chrome, without allowlisting theConfigure Malicious URL Blocking - VIPRE Security
To the Cisco IOS Network Management Command Reference. SUMMARY STEPS1. enable 2. configure terminal 3. cwmp agent 4. management server url acs-url 5. management server password [encryption-type | cleartext-password] passwd 6. provision code code-string 7. exit 8. interface type number 9. cwmp wan 10. cwmp wan default 11. exit 12. cwmp agent 13. enable download 14. session retry limit session-count 15. request outstanding request-count 16. parameter change notify interval time-interval 17. end DETAILED STEPS Command or ActionPurposeStep 1 enable Example:Device> enable Enables privileged EXEC mode. Enter your password if prompted. Step 2 configure terminal Example:Device# configure terminal Enters global configuration mode. Step 3 cwmp agent Example:Device(config)# cwmp agent Enables TR-069 Agent configuration mode. Step 4 management server url acs-url Example:Device(config-cwmp)# management server url Example:Device(config-cwmp)# management server url Specifies the HTTP/HTTPS URL to reach the ACS. This URL is used by the CPE to establish the TR-069 session with the ACS. Step 5 management server password [encryption-type | cleartext-password] passwd Example:Device(config-cwmp)# management server password 0 cisco Specifies the CPE password that is used in the authentication phase. This password will be provided to the ACS when the CPE is challenged for credential as part of authentication during the session establishment. Step 6 provision code code-string Example:Device(config-cwmp)# provision code ABCD Specifies the provision code to be used by the CPE. Step 7 exit Example:Device(config-cwmp)# exit Exits TR-069 Agent configuration mode and returns to global configuration mode. Step 8 interface type number Example:Device# interface serial 0/0 Enters interface configuration mode. Step 9 cwmp wan Example:Device(config-if)# cwmp wan (Optional) Defines the WAN interfaces on the CPE. Note Any interface without this command is considered a LAN interface by TR-069 protocol. There can be multiple WAN and LAN interfaces configured on the CPE. By default, an ATM interface on the CPE will be considered a WAN interface by the TR-069 protocol. Step 10 cwmp wan default Example:Device(config-if)# cwmp wan default Defines the default WAN interfaces on the CPE device. Note Among the multiple WAN interfaces, there can be only one default WAN interface in which the TR-069 communication could happen. If you try to configure this command on multiple interfaces, only the latest configuration will be active and the previous default WAN interface will become a WAN interface, ensuring only one interface is the default at any point in time. Step 11 exit Example:Device(config-if)# exit Exits interface configuration mode and returns to global configuration mode.5.6.3 Configure URL Blocking : TestOut - YouTube
From viruses and malicious content found on some websites. To enable web filtering for your organization, tick the checkbox Enable web filter. How do I configure Web filtering? How do I configure Web filtering? Web filtering can be done by two approaches: (1) allowing all websites and selectively blocking some (default, suitable for work environments), and (2) blocking all and selectively allowing some (suitable for educational institutions). Approach 1: Allow access to all websites and add rules to block certain websites By default, Puffin users are allowed to access all websites. When visiting Web filtering for the first time, the default rule ALLOW * is placed at the bottom. How to add a new rule: Scroll to Add a new filtering rule.(Optional) Set the position you want to insert the rule. The default is 1, at the top.Toggle the dropdown list to select ALLOW or BLOCK. When no option is selected, BLOCK takes precedence.Enter the domain, hostname, or URL you want to include in the rule.Click Add.The rule is added. It will take effect after users relaunch their Puffin Secure Browser. Note: For blocking rules to work properly, the rule ALLOW * must stay at the bottom of the list, indicating that it is the last rule for the web filtering service to check. Tip:The page includes instructions on the URL formats that Puffin Enterprise Cloud Portal supports. You can also refer to the Work with URL formats section for further details. Approach 2: Block access to all websites and add rules to allow certain websites In educational institutions, educators may want to only whitelist certain educational websites and block juvenile students' access to inappropriate websites. In this case, the default rule ALLOW * should be removed before the rule BLOCK *, which blocks access to all websites, can beConfiguring URL Blocking on pfSense Lab Report
Client Shop Floor Insight 7.12 with Quality Inspector and Job Tasks Modify the Shop Floor Insight Client Credentials 1. Before you Begin with Shop Floor Insight 2. Installing Shop Floor Insight 3. Registering Shop Floor Insight 4. Configure Special Permissions in Shop Floor Insight 5. Configure Paycodes in Shop Floor Insight 6. Configure Activity Codes in Shop Floor Insight 7. Configure Shifts in Shop Floor Insight 8. Configure Shop Floor Employees in Shop Floor Insight 9. Configure Work Centers in Shop Floor Insight 10. Configure Client Configuration in Shop Floor Insight 11. Configure Time Zone in Shop Floor Insight Install and Configure Shop Floor Insight (SaaS) 13. Print Barcodes and Smoke Test in Shop Floor Insight How to do an upgrade to the Shop Floor Insight Windows service Shop Floor Insight Communication App Requirements Set Up Facial Recognition Install and Configure Shop Floor Insight (On Prem) Show all articles ( 2 ) Collapse Articles 1. Before You Begin with Shop Floor Insight 2. Navigating Business Central in Shop Floor Insight 3. Process Overview in Shop Floor Insight 4. Printing Barcodes in Shop Floor Insight 5. Tour of the Shop Floor Interface 6. Capture Shop Floor Data for Production Orders in Shop Floor Insight 7. Capturing Job Time in Shop Floor Insight 8. Closing Time Cards in Shop Floor Insight 9. Approving Time Cards in Shop Floor Insight 10. Calculate Overtime in Shop Floor Insight 11. Posting Shop Floor Data in Shop Floor Insight 12. Export Time in Shop Floor Insight Configure Output Clock on Behavior Add a Non-Productive Activity Code Shop Floor Insight: Use the Mobile Interface Without a Phone Shop Floor Insight: Shop Floor Native Phone Client Shop Floor Insight's Published Events Show all articles ( 2 ) Collapse Articles How to Record Consumption Filtering Production Orders Adding a New Employee & Printing a Barcoded Badge How to Record Output The Supervisor / Employee Relationship Using Links in Shop Floor Insight Client Configuration Cards Shop Floor Activities Line Coloring How to Record a Comment Printing a Production Order Job Card Quality Inspections when Recording Output Changing the Work or Machine Center by Scanning a Barcode Dispatch List Filtering Automatically Assign Work and Machine Centers Time Card Line Rounding for Job Tasks Line Rounding of First Time Card Line Time Card Approval Process and Worksheet Include Other Paycodes for Overtime Calculations Automatic Filler Time Functionality Time Card Line Rounding for Shift Breaks Show all articles ( 6 ) Collapse Articles 401 Error Messages in Shop Floor Insight Troubleshoot Shop Floor Insight Issues How to troubleshoot "(400) Bad Request" errors in Shop Floor Insight Shop Floor Insight: Error Messages and Fixes Resolve URL ACL Issues Troubleshoot SSL Certificate Advanced Inventory Count Welcome to the Insight Works' Support Knowledge Base Release Notes: Advanced Inventory Count Install Advanced Inventory Count 3. Setup Wizard Introduction: Advanced Inventory Count 3. Module Design 4. Performing a Full Count 5. Performing a Cycle Count 6. Inventory Counts with WHI 7. Appendix A – Report Options Setting InventoryConfiguring Forefront TMG to block specific Websites (URL)
This is the latest build of MC27 for Linux. Please post bugs here. Please start a new thread for anything requiring discussion. Non-bug posts will be deleted.Download:amd64 in the Beta and Latest repos.27.0.66 (2/12/2021)1. Changed: Changed the Share toolbar button image.2. NEW: Added a "Shared" field that gets checked when you share, but if you uncheck the file will no longer be accessible.3. Fixed: Expressions that ended with a slash could output garbage.4. Changed: The optional 6 dB boost applied to DSD playback is reported in Audio Path.5. Fixed: Bug in DLNA conversion to DSF that resulted in popping especially at the end of a file.6. NEW: When playing a DMS channel associated with a DMS device, the IP address of the channel is checked against the device's current IP address. If the two are different, MC automatically updates the channel URL to match the device.7. Changed: Updated Russian translation (thanks Vladimir).8. Changed: Removed the URLs from the share dialog.9. NEW: Added "Share" toolbar buttons.10. Changed: Added URL escapement to the share URLs.11. Changed: When sharing, a choice is offered about what link to place on the clipboard.12. Changed: Renamed getting a file URL to "Share...".13. NEW: Generated a new file sharing MCWS call that does not require authentication. The file key is encrypted.14. NEW: When sharing, a local IP is also provided along with the remote IP.15. Fixed: Fast forward / rewind did not work when playing a DMS TV channel.16. Changed: Showing the day for a year only date will show an empty string instead of one.17. NEW: Added a way to reset your sharing credentials to Options > Media Network (will make all previous shares invalid).18. Changed: When opening 3 or 5 channel files, we will try to auto-configure as 5.1 and offer that as one of the choices.19. Changed: When opening 7 channel files, we will try to auto-configure as 7.1 and offer that as one of the choices.20. Changed: Tweaked the text of the auto-configure dialog to be more clear and to not report the bitdepth (since that isn't the actual output bitdepth).21. Fixed: Google lyrics lookup could contain junk at the end of the lyrics.22. Changed: MCWS no longer requires authentication for functions marked to not require authentication.23. NEW: Added the right-click command Get Sharing URL... to get a URL from MCWS to share externally (it uses your external IP address, so you will need to setup port forwarding on your router).24. Fixed: TV Channel grouping did not work with DMS channels.25. NEW: When running "Auto Group" on all TV channels, users are presented with a list of tuner types to select, so one can choose which types of channels are included in the auto group process.27.0.61 (2/4/2021)1. Fixed: Lyrics lookups stopped working.2. Changed: When opening 3 or 5 channel files, we will try to auto-configure as 5.1 and offer that as one of the choices.3. Changed: When opening 7 channel files, we will try to auto-configure as 7.1 and offer that as one. 4. The below Skype for business Configuration Information window opens. 3. 5. Check the EWS Internal URL and EWS External URL parameter in the configuration window (Highlighted in Yellow) 1. 6. If the users
Blocking URLs with JSON and App Configurations – Esper Help
Video Tutorial:What’s NeededWhat Requires Your Focus?Different Methods to Block Calls from an Area Code on AndroidWhy Can’t I Block Calls from an Area Code on Android?Implications and Recommendations:5 FAQs about Blocking Calls from an Area Code on AndroidFinal WordsAre you tired of receiving spam calls from particular area codes? Well, you are not alone. Spam calls are not only frustrating but also pose a significant security risk. A large percentage of scammers use area codes to target unsuspecting victims. Fortunately, Android phones have a built-in feature that allows you to block calls and messages from specific phone numbers, including area codes. In this guide, we will show you how to block calls from an area code on Android devices.Video Tutorial: What’s NeededTo block calls from an area code on Android, you’ll need the following:An Android phoneCall-blocking app (optional)Access to phone settingsWhat Requires Your Focus?Before delving into the different methods, you should focus on the following:Ensure that you have the correct area code that you want to block.Ensure that you do not block essential calls from areas you frequently receive calls.Consider installing a call-blocking app if the built-in feature does not offer adequate protection.Update your phone software regularly to ensure that you have the latest features and security patches.Different Methods to Block Calls from an Area Code on AndroidMethod 1: Using Phone Settings1. Open the phone app on your Android device.2. Tap the three vertical dots on the top right corner.3. Select “Settings” from the drop-down menu.4. Scroll down and select “Blocked numbers.”5. Tap “Add a number.”6. Type in the area code you want to block.7. Tap “Block.”8. Repeat steps 6-7 for additional area codes you want to block.Pros:– Built-in feature that is easy to use.– No need to install additional apps.– Provides a straightforward way to block calls from specific area codes.Cons:– Limited to blocking entire area codes, and not specific numbers.– Requires regular updating of blocked numbers to ensure maximum protection.Method 2: Using Call-Blocking Apps1. Search for a call-blocking app on Google Play Store.2. Download and install the app on your Android device.3. Open the app and configure the settings.4. Search and block the area codes from which you want to cease calls.Pros:– Provides additional security features such as SMS spam filters.– Some apps can block calls and messages from specific phone numbers and area codes.– Can detect potential spam calls from unfamiliar numbers.Cons:– Some call-blocking apps require in-app purchases to access premium features.– Some apps may cause device battery drain if not optimized.Method 3: Contacting Your Carrier1. Contact your service provider.2. Request them to block calls from a particular area code.3. Provide the area code you want to block.4. Follow up to ensure that the issue is resolved.Pros:–Blocking URLs with JSON and App Configurations Esper Help
How to Unblock Instagram on School Chromebook without VPN?As a student, it can be frustrating to be blocked from accessing your favorite social media platforms, including Instagram, on your school Chromebook. While some schools may block certain websites to promote productivity and focus, there are still ways to access Instagram without using a VPN (Virtual Private Network). In this article, we’ll explore the methods to unblock Instagram on your school Chromebook without VPN.Method 1: Check if Instagram is Blocked by the SchoolBefore trying any methods, it’s essential to check if Instagram is indeed blocked by the school. You can do this by trying to access Instagram on your school Chromebook. If you can’t access it, then it’s likely blocked.Method 2: Use the Chrome Extension "HTTPS Everywhere"One of the simplest ways to bypass website blocking is by using the Chrome extension "HTTPS Everywhere". This extension forces websites to use HTTPS, which is a more secure protocol than HTTP. As a result, some school filters may not be able to detect and block the website.To install "HTTPS Everywhere" on your school Chromebook:• Open the Chrome browser and go to the Chrome Web Store.• Search for "HTTPS Everywhere" and click on the "Add to Chrome" button.• Click on the "Add extension" button to confirm the installation.Once installed, you can access Instagram by going to instead of 3: Use the Incognito ModeAnother way to bypass website blocking is by using the Incognito mode in Chrome. This mode allows you to browse the internet without storing any of your browsing history, cookies, or data.To access Instagram in Incognito mode:• Open the Chrome browser and click on the three vertical dots in the top right corner.• Click on "New incognito window" to open a new Chrome window in Incognito mode.• Go to or to access Instagram.Method 4: Use the URL Redirect TrickSome school filters may block Instagram based on its URL. By using the URL redirect trick, you can bypass the blocking by redirecting the URL to a different address.To use the URL redirect trick:• Go to or and create a new URL redirect.• Enter the URL of Instagram ( and create a new short URL.• Use the new short URL to access Instagram.Method 5: Contact Your School AdministratorIf none of the above methods work, you can try contacting your school administrator to request unblocking of Instagram. You can explain the importance of social media for your personal and academic life, and ask if there’s an alternative solution that can be implemented.Table: Comparison of MethodsMethodEase of UseEffectivenessVPN RequiredHTTPS EverywhereEasy70%NoIncognito ModeEasy80%NoURL Redirect TrickMedium60%NoContact School AdministratorDifficult90%NoConclusionWhile there are no guarantees that these methods will work, they can increase your chances of accessing Instagram on your school Chromebook without. 4. The below Skype for business Configuration Information window opens. 3. 5. Check the EWS Internal URL and EWS External URL parameter in the configuration window (Highlighted in Yellow) 1. 6. If the usersConfigure Google Chrome with block/allow URLs and default
SecureAuth IdP 9.3Integrations: A to KCisco AnyConnect VPN on ASA (IdP-initiated) integration guideIntroductionUse this guide to integrate Cisco AnyConnect VPN (SAML) with SecureAuth IdP on Cisco Adaptive Security Appliance (ASA).PrerequisitesSecureAuth IdP version 9.1 or later with a realm ready for the Cisco ASA integrationCisco accountSupported on Cisco ASA version 9.7.1 or later for both AnyConnect client and clientless SSL VPNCisco ASA configuration stepsThis section provides the information you need to configure SecureAuth IdP on Cisco ASA.1. Log in to the Cisco ASA box.2. From the command line, run the following commands below and in the remaining steps:– sh run webvpn saml3. Create a SAML identity provider, where UniqueName can be any name. This name is used in the SecureAuth IdP configuration section for the WSFed/SAML Issuer field on the Post Authenticaton tab.saml idp UniqueName4. Configure the SecureAuth IdP URLs.url sign-in sign-out Configure the Clientless VPN base URL.base-url Configure trustpoints between the SecureAuth IdP and ASA.trustpoint idp UniqueNametrustpoint sp asa_saml_sp7. Configure SAML timeout.timeout assertion 7200SecureAuth IdP configuration steps1. Log in to your SecureAuth IdP Admin console.Post Authentication tab2. Select the Post Authentication tab.3. In the Post Authentication section, make the following entry:a. Set Authenticated User Redirect to SAML 2.0 (IdP Initiated) Assertion.4. In the User ID Mapping section, make the following entries:a. Set User ID Mapping to Authenticated User ID.5. In the SAML Assertion / WS Federation section, make the following entries:a. Set the WSFed Reply To / SAML Target URL to the absolute URL of the application, to where end-users are redirected upon successful authentication.For example, Set the SAML Consumer URL to the Cisco URL used to accept a SAML assertion.For example, Set the WSFed/SAML Issuer to a unique name that identifies the SecureAuth IdP to the application (as the SAML ID).This value is shared with the application and can be any word, phrase, or URL, but must match exactly in the SecureAuth IdP and Cisco ASA configurations.For example, UniqueName is used in step 3 of the Cisco ASA configuration stepsd. Set the SAML Recipient to the identifiable information of the SAML Recipient, which usually maps to the SAML Consumer URL.For example, Set the SAML Audience to the base domain of the application.For example, Set the SP Start URL to the login URL for the application.This value enables appropriate redirection for normal login and SSO login experiences.For example,Comments
Step 1: FA-related configurations:- Configure SAML Identity Provider Settings on FA:1) Navigate to Authentication -> SAML IdP -> General.2) Enable the SAML Identity Provider portal.3) Fill in the server address [it is possible to use the FA IP where FortiWeb will connect to].4) At Default IdP certificate: choose the default IDP certificate.5) At Realms: select add Realm.6) Select OK to save the config.- Download the IDP certificate to the local machine: 1) Navigate to Certificate Management -> End Entities -> Local Services.2) Download the default IDP certificate used in the previous step to be uploaded later on FortiWeb.- Configure SAML Service Provider options:1) Navigate to Authentication -> SAML IdP -> Service Providers.2) Fill in the SP name.3) At IdP prefix: select create new IdP prefix then generate prefix.4) Copy all of [IdP entity id, IdP single sign-on URL, IdP single logout URL] to an external notepad.5) Select save then choose the IdP prefix that was generated in step 3 again.6) Fill in SP options manually according to the following: 6.1) SP entity ID: [x.x.x.x is the FortiWeb IP]. 6.2) SP ACS (login) URL: 6.3) SP SLS (logout) URL: Configure FortiAuthenticator local users:1) Navigate to Authentication -> User Management -> Local User.2) Configure the required users.Step 2: FortiWeb-related Configurations:- Configure FortiWeb Fabric Connector:1) Navigate to Security Fabric -> Fabric Connectors.2) Leave the status 'disabled'.3) Ignore the options related to FortiGate Fabric [Upsteam IP, Management IP].4) Enable Single Sing-On Mode.5) Configure the SP Address as the FortiWeb Address.6) Fill in the [IDP Entity ID, IDP Single Sign-On URL, IDP Single Logout URL] according to the URLs copied in Step 1 Section 3.7) Upload the certificate downloaded in Step 1 Section (2) at IDP Certificate.- Perform the SSO login:1) Navigate to the FortiWeb login page.2) Select Via Single Sign-On.- Assign the user a full access privilege if required or a custom privilege:1) Log in to FortiWeb with the regular admin account.2) Navigate to System -> Admin -> Administrator.3) The SSO new account can be found under the SSO Admin tab.4) Assign to the user the required profile.Troubleshooting:- After selecting 'Via Single Sign-On' at the FortiWeb login page, it will not be redirected to the FA login page:- Review the SAML URLs at Security Fabric -> Fabric Connectors. Make sure it exactly matches the URLs extracted from FA at Authentication -> SAML IdP -> Service Providers.- Check the SP address on FortiWeb at Security
2025-03-30As the primary edge port when the interface has no external REP neighbor: Switch# configure terminal Switch (conf)# interface gigabitethernet1/1 Switch (conf-if)# rep segment 1 edge no-neighbor primary Switch (conf-if)# rep stcn segment 2-5 Switch (conf-if)# rep block port 0009001818D68700 vlan all Switch (conf-if)# rep preempt delay 60 Switch (conf-if)# rep lsl-age-timer 6000 Configuring VLAN Blocking: Example This example shows how to configure the VLAN blocking configuration shown in Figure 23-5. The alternate port is the neighbor with neighbor offset number 4. After manual preemption, VLANs 100 to 200 are blocked at this port, and all other VLANs are blocked at the primary edge port E1 (Gigabit Ethernet port 1/0/1). Switch# configure terminal Switch (conf)# interface gigabitethernet1/1 Switch (conf-if)# rep segment 1 edge primary Switch (conf-if)# rep block port 4 vlan 100-200 Switch (conf-if)# end Figure 23-5 Example of VLAN Blocking Additional References The following sections provide references related to switch administration: Related Documents Related Topic Document Title Cisco IE 2000 commands Cisco IE 2000 Switch Command Reference, Release 15.0(1)EY Cisco IOS basic commands Cisco IOS Configuration Fundamentals Command Reference Standards Standards Title No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature. — MIBs MIBs MIBs Link — To locate and download MIBs using Cisco IOS XR software, use the Cisco MIB Locator found at the following URL and choose a platform under the Cisco Access Products menu: RFCs RFCs Title No new or modified RFCs are supported by this feature, and support for existing RFCs has not been modified by this feature. —
2025-04-13To the Cisco IOS Network Management Command Reference. SUMMARY STEPS1. enable 2. configure terminal 3. cwmp agent 4. management server url acs-url 5. management server password [encryption-type | cleartext-password] passwd 6. provision code code-string 7. exit 8. interface type number 9. cwmp wan 10. cwmp wan default 11. exit 12. cwmp agent 13. enable download 14. session retry limit session-count 15. request outstanding request-count 16. parameter change notify interval time-interval 17. end DETAILED STEPS Command or ActionPurposeStep 1 enable Example:Device> enable Enables privileged EXEC mode. Enter your password if prompted. Step 2 configure terminal Example:Device# configure terminal Enters global configuration mode. Step 3 cwmp agent Example:Device(config)# cwmp agent Enables TR-069 Agent configuration mode. Step 4 management server url acs-url Example:Device(config-cwmp)# management server url Example:Device(config-cwmp)# management server url Specifies the HTTP/HTTPS URL to reach the ACS. This URL is used by the CPE to establish the TR-069 session with the ACS. Step 5 management server password [encryption-type | cleartext-password] passwd Example:Device(config-cwmp)# management server password 0 cisco Specifies the CPE password that is used in the authentication phase. This password will be provided to the ACS when the CPE is challenged for credential as part of authentication during the session establishment. Step 6 provision code code-string Example:Device(config-cwmp)# provision code ABCD Specifies the provision code to be used by the CPE. Step 7 exit Example:Device(config-cwmp)# exit Exits TR-069 Agent configuration mode and returns to global configuration mode. Step 8 interface type number Example:Device# interface serial 0/0 Enters interface configuration mode. Step 9 cwmp wan Example:Device(config-if)# cwmp wan (Optional) Defines the WAN interfaces on the CPE. Note Any interface without this command is considered a LAN interface by TR-069 protocol. There can be multiple WAN and LAN interfaces configured on the CPE. By default, an ATM interface on the CPE will be considered a WAN interface by the TR-069 protocol. Step 10 cwmp wan default Example:Device(config-if)# cwmp wan default Defines the default WAN interfaces on the CPE device. Note Among the multiple WAN interfaces, there can be only one default WAN interface in which the TR-069 communication could happen. If you try to configure this command on multiple interfaces, only the latest configuration will be active and the previous default WAN interface will become a WAN interface, ensuring only one interface is the default at any point in time. Step 11 exit Example:Device(config-if)# exit Exits interface configuration mode and returns to global configuration mode.
2025-04-20From viruses and malicious content found on some websites. To enable web filtering for your organization, tick the checkbox Enable web filter. How do I configure Web filtering? How do I configure Web filtering? Web filtering can be done by two approaches: (1) allowing all websites and selectively blocking some (default, suitable for work environments), and (2) blocking all and selectively allowing some (suitable for educational institutions). Approach 1: Allow access to all websites and add rules to block certain websites By default, Puffin users are allowed to access all websites. When visiting Web filtering for the first time, the default rule ALLOW * is placed at the bottom. How to add a new rule: Scroll to Add a new filtering rule.(Optional) Set the position you want to insert the rule. The default is 1, at the top.Toggle the dropdown list to select ALLOW or BLOCK. When no option is selected, BLOCK takes precedence.Enter the domain, hostname, or URL you want to include in the rule.Click Add.The rule is added. It will take effect after users relaunch their Puffin Secure Browser. Note: For blocking rules to work properly, the rule ALLOW * must stay at the bottom of the list, indicating that it is the last rule for the web filtering service to check. Tip:The page includes instructions on the URL formats that Puffin Enterprise Cloud Portal supports. You can also refer to the Work with URL formats section for further details. Approach 2: Block access to all websites and add rules to allow certain websites In educational institutions, educators may want to only whitelist certain educational websites and block juvenile students' access to inappropriate websites. In this case, the default rule ALLOW * should be removed before the rule BLOCK *, which blocks access to all websites, can be
2025-04-15